Recovering a closed browser window is a quick and simple task that anyone can master. The process varies slightly depending on the web browser you’re using, but most commonly, it involves straightforward steps that require minimal technical knowledge. For instance, in Google Chrome, you can easily restore a closed window by right-clicking on a blank space in the tab bar and selecting ‘Reopen closed tab’ or using the keyboard shortcut ‘Ctrl+Shift+T’.
Similarly, in Mozilla Firefox, you can restore your closed window by clicking on the menu button, selecting ‘History’, and then ‘Recently Closed Windows’. In Safari, select ‘History’ from the top menu and then ‘Reopen Last Closed Window’. This quick guide aims to equip you with the knowledge to retrieve closed browser windows in various browsers efficiently, saving you time and reducing any potential stress or frustration. It’s an invaluable skill that can help you recover lost work or accidentally closed tabs, ensuring a smoother and more convenient browsing experience.
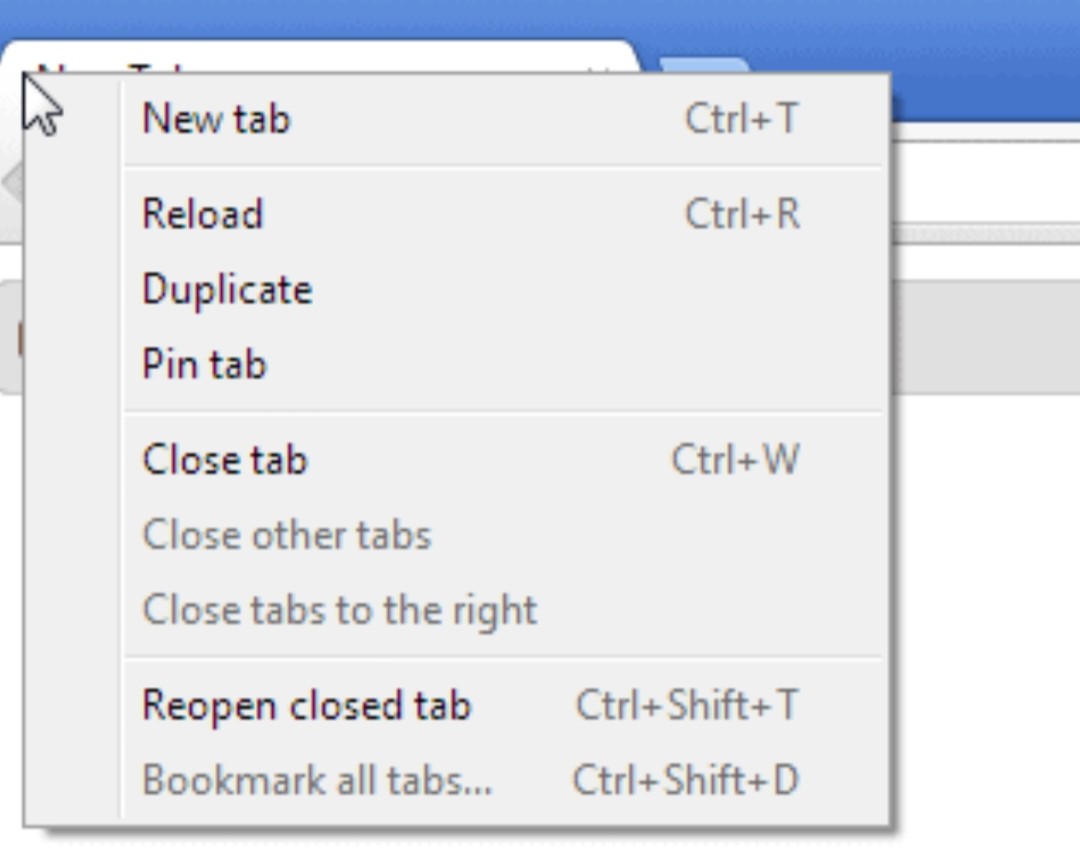
Utilizing Browser History
Utilizing browser history can be a valuable tool in various settings. In the digital era where the internet is a significant part of almost everyone’s life, browser history can offer insights into user behavior, preferences, and even predict future actions. However, it’s essential to remember that privacy concerns are paramount when dealing with such data. For individuals, browser history can serve as a helpful reminder of previously visited sites, useful when trying to locate a specific webpage or information. This feature can also enhance the user experience by providing personalized recommendations based on past browsing activities.
In business and marketing, the data from browser history can be used to create targeted advertising, which is more likely to engage the audience. It allows businesses to understand their customers better, leading to improved products and services. Furthermore, in the educational sector, teachers can use students’ browser histories to gauge their interests and tailor lessons accordingly. This individual approach can contribute to more engaging and effective learning.
In the realm of cybersecurity, analyzing browser history can play a crucial role in identifying potential threats and vulnerabilities. It can provide vital clues about suspicious activities and help devise strategies to counter cyber threats. Conversely, individuals should be aware that their browser history can be accessed by unauthorized parties, leading to potential privacy breaches. Therefore, it’s essential to regularly clear browser history and use secure browsing methods.
In conclusion, while the utilization of browser history comes with substantial benefits, it’s critical to handle such data with utmost care, considering the privacy implications. With the right approach, browser history can be a powerful tool for improving user experience, business operations, educational practices, and cybersecurity measures.
Keyboard Shortcuts for Recovery
Keyboard shortcuts for recovery play an essential role in enhancing productivity and efficiency while using a computer. They are particularly useful during instances where there are system crashes, accidental deletions or alterations, or when applications become unresponsive. These keystrokes are designed to trigger specific commands that enable the system or application to revert to a previous state, undo a recent action, or restore data.
For instance, the universal shortcut keys “Ctrl + Z” in Windows or “Command + Z” on Macs are used for undoing recent actions, which can be helpful in recovering data that was accidentally deleted or altered. Additionally, “Ctrl + Y” or “Command + Shift + Z” are used to redo actions, which can be useful in situations where you have unintentionally undone a necessary action.
In the event of system crashes or unresponsive applications, combinations like “Ctrl + Alt + Del” on Windows or “Command + Option + Esc” on Macs can help in recovering control over the system. These shortcuts allow users to access the Task Manager or Force Quit applications, enabling them to close unresponsive applications and avoid potential data loss.
System recovery options can also be accessed through keyboard shortcuts during startup. For instance, pressing “F8” during Windows startup allows users to enter Safe Mode, a diagnostic mode used for troubleshooting and recovery. Similarly, holding down the “Command + R” keys during Mac startup enables users to enter Recovery Mode, where they can repair disks or reinstall the operating system if necessary.
Overall, understanding and utilizing these keyboard shortcuts for recovery can significantly simplify the process of troubleshooting and data recovery. They not only save time but also reduce the risk of data loss, making them a valuable tool for any computer user.

Leveraging Browser Settings
Leveraging browser settings is an essential aspect of enhancing one’s internet browsing experience. It involves modifying and customizing the browser according to the user’s preferences to achieve optimal performance and user satisfaction. Different browsers offer various settings that can be adjusted to suit the user’s needs. These include security settings, privacy settings, display settings, and many others.
Taking advantage of these settings can significantly improve the browsing experience. For instance, adjusting the security settings can increase protection against harmful software and phishing attacks. This can be especially advantageous to users who frequently visit different websites, as it reduces the risk of encountering malicious content.
Privacy settings, on the other hand, allow users to control the data that websites can collect about them. By tweaking these settings, users can limit the information they share with websites, thereby enhancing their online privacy.
Display settings play a critical role in influencing the visual aspect of the browsing experience. Users can adjust these settings to ensure the content they view is displayed in a manner that suits their visual preferences. This can range from adjusting the size of the text to choosing a specific theme for the browser.
Leveraging browser settings also involves managing cookies and site data. This allows users to control the amount of information that websites remember about them, including login information and site preferences.
In conclusion, leveraging browser settings is a powerful tool that users can utilize to tailor their internet browsing experience to their specific needs and preferences. By understanding how to adjust these settings, users can significantly improve their online experience, enhance their privacy, and increase their protection against potential threats.
Exploring Session Restore Options
Session restore options are a crucial aspect of data management, particularly in business environments where data integrity and availability are often paramount. These options allow for the recovery of data that might have been lost or corrupted due to software malfunctions, hardware failures, or unexpected system shutdowns. Exploring session restore options involves understanding the different mechanisms available for data restoration, their benefits and limitations, and choosing the most suitable option for a specific scenario.
One commonly used session restore option is the automatic save and restore feature found in many software applications. This feature periodically saves the current session data and allows for its retrieval in case of an unexpected application or system shutdown. However, this option may not always guarantee the complete recovery of all data, especially if the data was not saved before the shutdown.
Another option for session restore is the use of backup and restore software. These tools can create a copy of all session data at regular intervals and store them in a separate location. In the event of data loss, the software can restore the session data from these backups. However, the effectiveness of this option depends on the frequency of backups and the reliability of the backup storage.
Cloud-based session restore options are also becoming increasingly popular. These options store session data in the cloud, which can be accessed and restored from any location with internet access. This eliminates the risk of data loss due to local hardware failures. However, cloud-based options might require a stable and fast internet connection to ensure seamless data recovery.
In conclusion, exploring session restore options involves the careful evaluation of different data recovery mechanisms, their reliability, and their suitability for specific scenarios. The choice of session restore option can significantly impact data integrity and availability, thus it should be made with thorough consideration.
Using Third-Party Extensions
Third-party extensions offer an array of benefits and potential drawbacks that users should be aware of. These tools, developed by entities that are not associated with the original software or program, can add functionality, customization, and enhancements to the primary platform. For instance, web browsers such as Chrome and Firefox support numerous third-party extensions that can improve user experience by blocking ads, managing tabs, and automating tasks.
However, it’s important to exercise caution when installing and using these add-ons. Some third-party extensions may contain malicious code, which can compromise the security of your system, expose sensitive information, or lead to unwanted changes in the applications’ behavior. It is thus crucial to ensure that the extensions come from reputable sources, have good user ratings and reviews, and have clear, understandable permissions.
Furthermore, the use of third-party extensions can sometimes lead to issues of compatibility and stability with the main software. Extensions might not always be up-to-date with the latest version of the software, causing glitches, crashes, or other functional problems.
In addition, privacy concerns are often associated with the use of third-party extensions. Many extensions require access to user data to function, and not all developers have the same standards or policies regarding data protection and privacy. Users should carefully read the privacy policies and terms of service before installing any extension.
Lastly, while many third-party extensions are free, some come with hidden costs such as in-app purchases or subscription fees. Users should be aware of these potential costs and decide whether the added functionality is worth the price.
In conclusion, third-party extensions can significantly enhance the functionality and usability of software and applications. However, users should exercise caution and make informed decisions when choosing and using these tools, taking into consideration factors such as security, privacy, compatibility, and cost.
Preventing Accidental Closures
Preventing accidental closures is a significant aspect of ensuring smooth operations, especially in technology and business operations. In the realm of technology, accidental closures could refer to the unintended shutting down of computer programs or applications that may lead to loss of unsaved work. This scenario can be prevented by implementing auto-save features, regular reminders for saving work, or confirmation pop-ups before closing an application.
In business operations, accidental closures may refer to the unintentional cessation of vital services or facilities. This can be avoided by establishing robust standard operating procedures, improving communication, and implementing checks and balances within the system. For instance, having a double-check system before shutting down any service can greatly reduce the chances of accidental closures. Regular maintenance and inspection of facilities can also preemptively identify and rectify any potential issues that may lead to accidental closures.
Similarly, in the context of physical spaces like shops or buildings, accidental closures can be prevented by adopting responsible practices such as double-checking locks, timers, and automated systems. Staff training and awareness are also key to ensuring that accidental closures do not occur – employees must be made aware of the repercussions of accidental closures, and trained on the correct protocols and procedures.
Therefore, preventing accidental closures, whether in the realm of technology, business operations, or physical spaces, is a matter of caution, vigilance, and responsible practices. It is crucial for the smooth running of operations, the prevention of data loss, and the maintenance of a reliable service or facility. It is a critical factor in reducing disruptions, maintaining productivity, and ensuring customer satisfaction. Therefore, a well-structured approach, regular training, and a culture of responsibility are key to preventing accidental closures.
